When you use a proxy or VPN, your connections are routed through a proxy server or a VPN server. Consequently, to the target host (web site or service), they look as though they came from the proxy's or VPN server's IP address. This prevents the target host from knowing your true IP address.
To make connections, your computer needs to know the IP addresses of the target hosts. This is where DNS comes into play. From a security standpoint, DNS requests (usually UDP packets on port 53) should go only through the same VPN or proxy connection. If DNS requests go through other routes, a DNS leak happens. This effectively means that your true location is revealed.
A DNS leak is also a security threat because the leaked DNS data are not secured by the VPN or the proxy. In public networks, it can be intercepted and analyzed.
Operating systems are optimized for performance, not for DNS leak prevention. In Windows, a DNS leak may be caused by the feature called Windows Multi-Homed DNS. The logic is simple - the system resolver sends the same DNS request over all available network connections on the system in an attempt to receive an answer as quickly as possible. This is good for performance but effectively creates a DNS leak. Even if this option is disabled, there is a logic that tells the resolver to fall back to the DNS server of the other connection if the primary one (VPN) times out. This condition may happen randomly due to an intermittent connectivity problem. To make matter worse, there are IPv4 and IPv6 addresses (A and AAAA DNS queries) whose handling depends on the current network conditions and capacities.
To illustrate the problem, we tested a built-in Windows 10 VPN (IKEv2/IPsec). The VPN server is located in France. The client's local DNS is in Finland.
There are a number of sites that can test for a DNS leak, for example, https://browserleaks.com/dns
The testing page displays the client's IP address, which is in France because of the VPN server's location, but DNS requests come from the client's DNS server (Finland) as well. This is a DNS leak.
If we run YogaDNS in bypass mode and check the log (verbose mode) generated through the test, we can see multiple records such as the following:
[03.05 15:40:06] krg5ju3lmloa3kgp2xzyeg3m591kpoge.dnsleak6.browserleaks.org - request : type=A, id=2872, server=103.86.96.100:53, program=svchost.exe, pid=1204 [03.05 15:40:06] krg5ju3lmloa3kgp2xzyeg3m591kpoge.dnsleak6.browserleaks.org - bypass : rule=Default [03.05 15:40:06] krg5ju3lmloa3kgp2xzyeg3m591kpoge.dnsleak6.browserleaks.org - request : type=A, id=49765, server=10.0.0.1:53, program=svchost.exe, pid=1204 [03.05 15:40:06] krg5ju3lmloa3kgp2xzyeg3m591kpoge.dnsleak6.browserleaks.org - bypass : rule=Default
It is clear that the Windows system resolver (svchost.exe) tries to resolve each hostname through two DNS servers (VPN 103.86.96.100 and local 10.0.0.1) at the same time. This causes a DNS leak, and the true location of the client is revealed.
YogaDNS provides an easy, quick, and reliable way to prevent DNS leaks. It can intercept all DNS requests on the system and forward them strictly through the specific DNS server. This eliminates DNS leaks because no other DNS servers will be used.
The setup is quite easy.
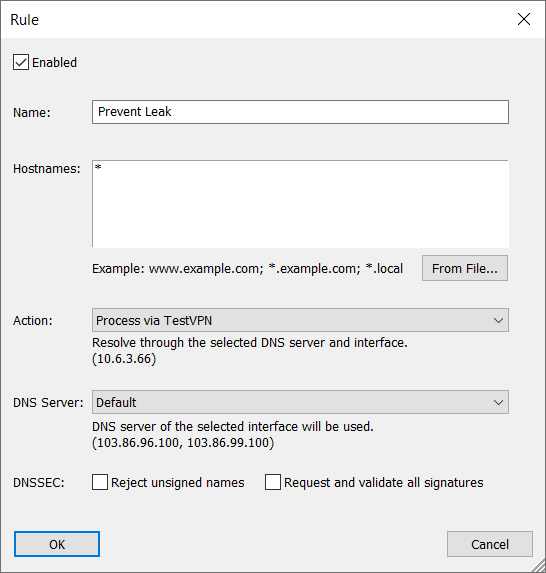 Rule to prevent a DNS leak
Rule to prevent a DNS leak
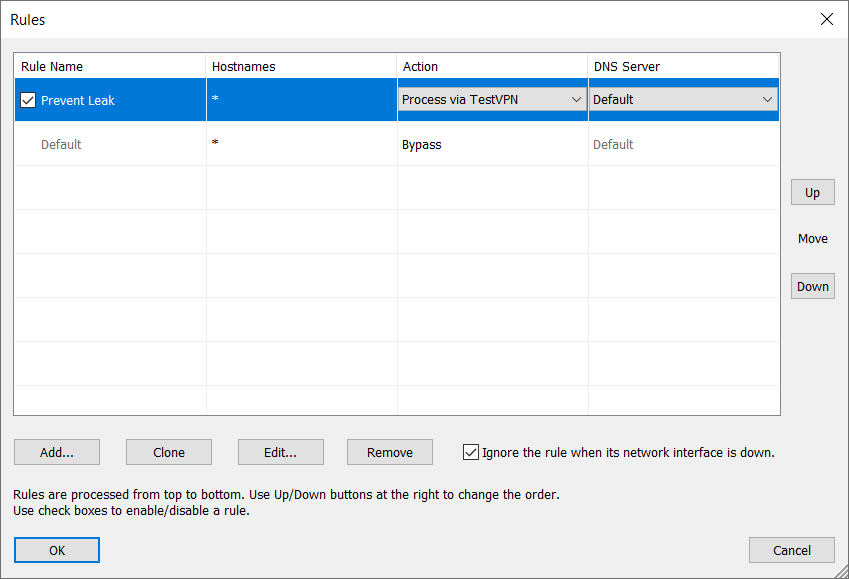
That's it. Now, if we repeat the DNS leak test, it will indicate no leak. The client's IP and the DNS server are in the same location. There are no other DNS servers detected.
In the YogaDNS log (verbose mode), the records will look like this:
[03.05 15:36:54] fkqbiv6hvqnrftyfo2bhf2fnbgbpomkr.dnsleak6.browserleaks.org - request : type=A, id=32085, server=103.86.96.100:53, program=svchost.exe, pid=1204 [03.05 15:36:54] fkqbiv6hvqnrftyfo2bhf2fnbgbpomkr.dnsleak6.browserleaks.org - process : server=103.86.96.100 (Plain, 103.86.96.100), interface=TestVPN (10.6.3.66), rule=Prevent Leak [03.05 15:36:54] fkqbiv6hvqnrftyfo2bhf2fnbgbpomkr.dnsleak6.browserleaks.org - request : type=A, id=4686, server=10.0.0.1:53, program=svchost.exe, pid=1204 [03.05 15:36:54] fkqbiv6hvqnrftyfo2bhf2fnbgbpomkr.dnsleak6.browserleaks.org - process : server=103.86.96.100 (Plain, 103.86.96.100), interface=TestVPN (10.6.3.66), rule=Prevent Leak
The system resolver (svchost.exe) still sends requests to two DNS servers (VPN 103.86.96.100 and local 10.0.0.1), but YogaDNS intercepts both requests and forces them through the DNS server of the VPN (103.86.96.100). Thus, there is no DNS leak.
YogaDNS allows you to add even more security and anonymity to DNS. Instead of a plain, unencrypted DNS protocol, you can use encrypted protocols: DNSCrypt and DNS over HTTPS. DNS data can be authenticated with DNSSEC.
The following is an example of a Swiss DNS over HTTPS server.
Your rule list will look like this:
Henceforth, YogaDNS will forward all DNS requests through the specified DNS server.
A DNS leak test will show that all queries are now processed by the DNS server located in Switzerland. Your local and VPN DNS servers will no longer be detected.
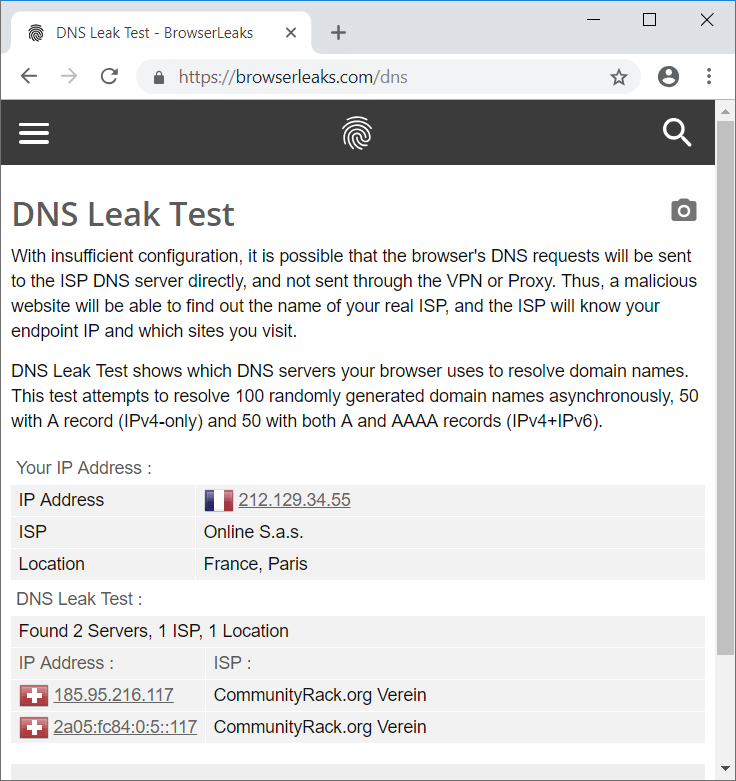 A DNS leak test shows the server in Switzerland
A DNS leak test shows the server in Switzerland
Yoga DNS log (verbose mode):
[03.06 13:42:28] q3rxd4q8lxim99xi88d3cyd8n9ynds6f.dnsleak4.browserleaks.org - request : type=A, id=15447, server=103.86.96.100:53, program=svchost.exe, pid=1204 [03.06 13:42:28] q3rxd4q8lxim99xi88d3cyd8n9ynds6f.dnsleak4.browserleaks.org - process : server=dns.digitale-gesellschaft.ch (DNS over HTTPS, https://dns.digitale-gesellschaft.ch/dns-query), interface=TestVPN (10.6.3.66), rule=Prevent Leak [03.06 13:42:28] q3rxd4q8lxim99xi88d3cyd8n9ynds6f.dnsleak4.browserleaks.org - request : type=A, id=23413, server=10.0.0.1:53, program=svchost.exe, pid=1204 [03.06 13:42:28] q3rxd4q8lxim99xi88d3cyd8n9ynds6f.dnsleak4.browserleaks.org - process : server=dns.digitale-gesellschaft.ch (DNS over HTTPS, https://dns.digitale-gesellschaft.ch/dns-query), interface=TestVPN (10.6.3.66), rule=Prevent Leak
At this point, you can anonymize DNS even further by using Anonymized DNS. In this scenario, YogaDNS will access the DNS server through a special relay server. This prevents DNS servers from learning anything about the client's IP address.