To resolve a hostname, a client computer queries a DNS server and receives an answer, e.g., an IP address. This logic is straightforward when there is only one network interface (a network connection, such as Ethernet, Wi-Fi, VPN, etc.) on the system. If there are multiple interfaces with multiple DNS servers, however, a number of questions and problems arise:
Unfortunately, there is no universal answer to these questions. In each case, the resolution logic depends on the network configuration and scenario.
The problems become even more prominent if a VPN connection is involved.
Windows uses a very complex logic for name resolution when dealing with multiple network interfaces.
The behavior can be changed from multiple points:
All of the above parameters are independent and may interfere with one another.
In our tests, Windows 10 with a default configuration and a VPN connection has sent DNS requests to all available DNS servers through all interfaces.
Below is a verbose log of the YogaDNS tool running in bypass mode.
[03.13 18:54:38] iana.org - request : type=A, server=103.86.96.100:53, program=svchost.exe [03.13 18:54:38] iana.org - bypass : rule=Default [03.13 18:54:38] iana.org - request : type=A, server=10.0.0.1:53, program=svchost.exe [03.13 18:54:38] iana.org - bypass : rule=Default [03.13 18:54:38] iana.org - reply (direct) : type=A, ips=192.0.43.8 [03.13 18:54:38] iana.org - reply (direct) : type=A, ips=192.0.43.8
It is clearly visible that the Windows system resolver (svchost.exe) tries to resolve the same hostname (iana.org) through two DNS servers (VPN 103.86.96.100 and Ethernet 10.0.0.1) at the same time. Both servers return the same answer. If the hostname belonged only to the LAN of the VPN, it would effectively mean that the name would be revealed to the public network. This condition is also known as DNS Leak.
Under some conditions or due to an incorrect configuration, Windows may stick to the DNS server of only a specific connection and ignore all other DNS servers. It may prevent the client from resolving hostnames that are serviced only by a specific DNS server (e.g., LAN internal names).
Another problem may arise when a single hostname resolves to different IP addresses inside and outside the LAN.
All problems of DNS resolution through multiple network interfaces can be easily solved with YogaDNS, a small software tool with an easy yet powerful UI that can transparently intercept DNS queries from apps and system resolver and process them according to user-defined rules. With YogaDNS you can:
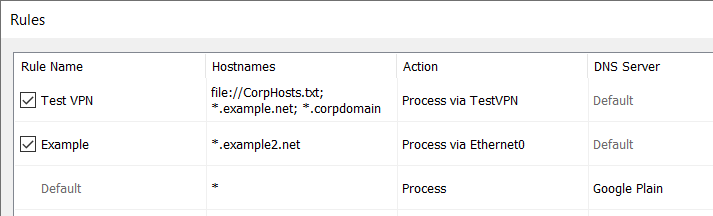

For a test, we take a Windows 10 system with Ethernet and VPN connections. Assume that the VPN connects to a corporate LAN with domains such as *.corpdomain.
Below is an example of two resolutions: test.corpdomain and iana.org.
[03.19 16:15:07] test.corpdomain - request : type=A, id=9239, server=103.86.99.100:53, program=svchost.exe, pid=1272 [03.19 16:15:07] test.corpdomain - bypass : rule=Default [03.19 16:15:07] test.corpdomain - request : type=A, id=50817, server=10.0.0.1:53, program=svchost.exe, pid=1272 [03.19 16:15:07] test.corpdomain - bypass : rule=Default [03.19 16:15:07] test.corpdomain - reply (direct) : type=A, id=50817, ips= [03.19 16:15:07] test.corpdomain - reply (direct) : type=A, id=9239, ips=192.172.1.7 [03.19 16:15:11] iana.org - request : type=A, id=36739, server=103.86.99.100:53, program=svchost.exe, pid=1272 [03.19 16:15:11] iana.org - bypass : rule=Default [03.19 16:15:11] iana.org - request : type=A, id=18268, server=10.0.0.1:53, program=svchost.exe, pid=1272 [03.19 16:15:11] iana.org - bypass : rule=Default [03.19 16:15:11] iana.org - reply (direct) : type=A, id=18268, ips=192.0.43.8 [03.19 16:15:11] iana.org - reply (direct) : type=A, id=36739, ips=192.0.43.8
It is clear that Windows tries to resolve all the names through both interfaces at the same time. Thus, queries for test.corpdomain and iana.org go to two DNS Servers: 103.86.99.100 (VPN) and 10.0.0.1 (Ethernet).
As described above in this article, this situation is suboptimal and may lead to security and performance problems.
To solve all these problems, you can simply create a single rule in YogaDNS, which will indicate that all the names that match *.corpdomain should be resolved through the VPN interface.
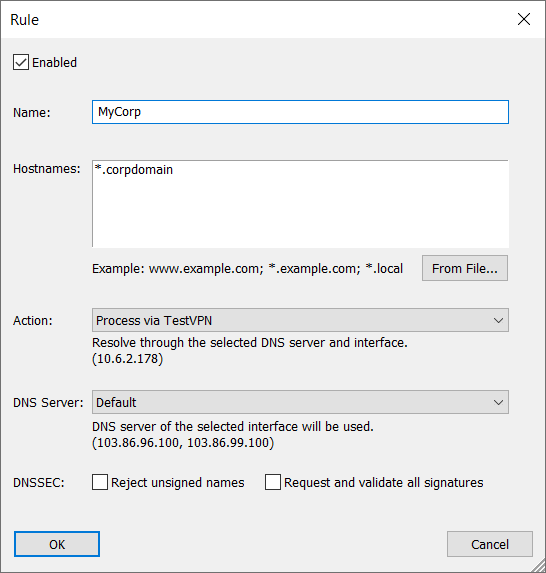
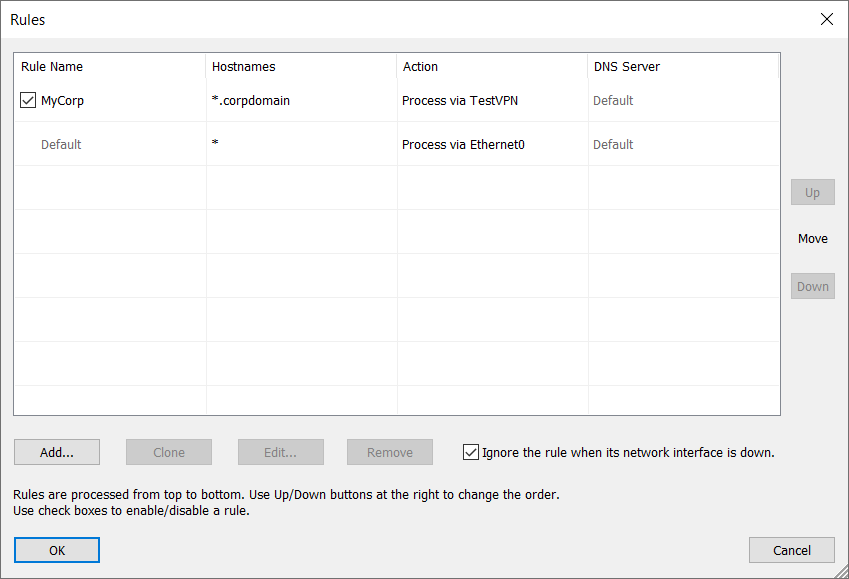
That's it. Now, if we repeat the test again in the debug log, it is clear that Windows still tries to resolve using both interfaces and DNS servers, but YogaDNS forces the requests as specified by the rules.
[03.19 16:34:15] test.corpdomain - request : type=A, id=62391, server=103.86.96.100:53, program=svchost.exe, pid=1272 [03.19 16:34:15] test.corpdomain - process : server=103.86.96.100 (Plain, 103.86.96.100), interface=TestVPN (10.6.2.178), rule=MyCorp [03.19 16:34:15] test.corpdomain - request : type=A, id=15697, server=10.0.0.1:53, program=svchost.exe, pid=1272 [03.19 16:34:15] test.corpdomain - process : server=103.86.96.100 (Plain, 103.86.96.100), interface=TestVPN (10.6.2.178), rule=MyCorp [03.19 16:34:15] test.corpdomain - reply : type=A, id=9, ips=192.172.1.7 [03.19 16:34:15] test.corpdomain - reply : type=A, id=10, ips=192.172.1.7 [03.19 16:34:17] iana.org - request : type=A, id=28618, server=103.86.96.100:53, program=svchost.exe, pid=1272 [03.19 16:34:17] iana.org - process : server=10.0.0.1 (Plain, 10.0.0.1), interface=Ethernet0 (10.0.0.100), rule=Default [03.19 16:34:17] iana.org - request : type=A, id=3671, server=10.0.0.1:53, program=svchost.exe, pid=1272 [03.19 16:34:17] iana.org - process : server=10.0.0.1 (Plain, 10.0.0.1), interface=Ethernet0 (10.0.0.100), rule=Default [03.19 16:34:17] iana.org - reply : type=A, id=11, ips=192.0.43.8 [03.19 16:34:17] iana.org - reply : type=A, id=12, ips=192.0.43.8
Thus, test.corpdomain gets resolved only through the VPN connection (DNS server 103.86.96.100), and iana.org gets resolved only through the Ethernet connection (DNS server 10.0.0.1).
With YogaDNS, you can create much more complex rules, include hostnames from files, use the DNSCrypt and DNS over HTTPS protocols, and use DNSSEC.